DORA Proportionality: Right-Sizing Compliance for FinTechs
DORA Proportionality made practical: CTO roadmap to tailor ICT risk controls, automate incident reporting, and streamline third-party oversight for audits.
How to Master DORA Proportionality: A CTO’s Practical Guide
1. Know the Legal Bedrock
Recital 36 — The Intent
“Financial entities shall put in place and maintain resilient ICT systems taking into account the nature, scale and complexity of their services, activities and operations, as well as their overall risk profile.”
Share this exact wording whenever someone treats DORA as a one-size-fits-all rulebook.
Article 4 — The Mandate
Supervisors must assess compliance “in a proportionate manner,” weighing:
nature, scale and complexity of services
overall risk profile
potential impact on customers and markets
Article 16 — The Safety Valve for Micro & Small Firms
Entities with fewer than 10 staff and an annual turnover below €2 million may use a simplified ICT-Risk Management Framework (ICT-RMF). They are exempt from Articles 5–15 (including TLPT) provided they maintain basic security-by-design controls and an incident log.
Quick Win — Circulate the Excerpts
Create a two-page brief containing Recital 36, Article 4 and Article 16; highlight key phrases and send it to executives and legal counsel before budget talks.
Mini-Checklist for CTOs
Recital 36 archived in the policy wiki
Excerpts included in the next board deck
Internal FAQ entry: “Proportionality is built into DORA—see Recital 36, Art. 4 & 16”
2. Profile Your Size-Risk Matrix
Why Start Here?
Regulators expect an up-front self-assessment. Skipping it invites over-engineering—or blind spots.
Step-by-Step Mapping
List core assets — systems, code repos, on-prem hardware, SaaS.
Capture transaction volumes — daily payments, peak API calls.
Mark geographic scope — customer countries, data-centre locations.
Identify critical functions — activities whose failure halts payments, trading or onboarding.
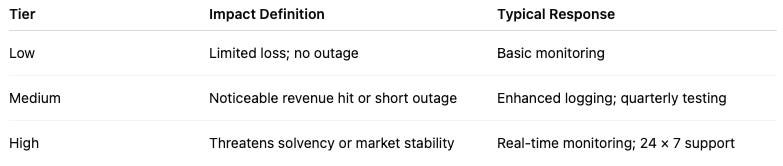
Classify Impact Tiers
Mini-Checklist
Matrix covers 100 % of production assets
Impact tier agreed by two + stakeholders
Reviewed quarterly or after material changes
3. Governance Guard-Rails (Article 5)
The board remains ultimately accountable for ICT risk:
An accountable executive (CTO, CIO or COO) is formally appointed.
The three lines of defence model is respected: operations, risk-control, and internal audit.
The board approves and publishes the underlying assumptions of the size-risk matrix every year.
Mini-Checklist
Board minutes reflect an annual ICT-risk review
First- and second-line roles separated by policy or contract
4. Tailor Your ICT-RMF (Article 6)
Article 6 demands an ICT-Risk Management Framework but explicitly allows scalability based on “size, risk profile and business complexity.” You can extend existing cyber- or operational-risk processes instead of starting from scratch.
Reminder: If you qualify for Article 16, the entire framework can often be compressed into a single 10–15-page integrated policy.
Minimum Viable Controls Every CTO Must Evidence
Even the leanest ICT-RMF must demonstrably cover the six NIST-style functions:
5. Scale Incident Reporting (Articles 19–20)
Match the Clock to Your Size
The final RTS (17 July 2024) sets strict windows:
4 hours after designating an incident as major — initial notification
24 hours after detection — if classification is still pending
If a deadline falls on a non-business day, most entities (except significant/systemic ones) may report by 12:00 on the next working day
Automate Severity Mapping
A rules engine that weighs service impact, customer reach, and data loss can instantly tag incidents as major or significant, ensuring only genuinely major events trigger the 4-hour clock.
Keep One Taxonomy — DORA, GDPR, NIS2
Align labels so one incident equals one record. The Commission explicitly encourages converged taxonomies.
6. Calibrate TLPT & Testing (Article 26)
Document your rationale and keep evidence for auditors.
7. Streamline Third-Party Oversight (Articles 28–31)
Quick Risk Triage
List all external ICT services.
Score criticality: core, important or supporting.
Scale due diligence accordingly.
Risk-Based Due Diligence
Mandatory Contract Clauses (Article 30 § 2)
Every contract covering a critical or important service must include:
audit and inspection rights
conditions for sub-outsourcing
data location and portability requirements
incident-notification timelines
exit and transition plan
8. Evidence Your Decisions
Regulators want the logic behind scaled controls. Annotate each control with its link to the size-risk matrix and refresh documentation quarterly. All controls must be fully in force or explicitly scheduled.
9. Tap Guidance & Peers
Reg-Tech sandboxes, industry round-tables and peer benchmarks are excellent ways to pressure-test proportionality decisions before audits.
10. Build a Three-Year Maturity Roadmap
KPIs should track impact (e.g., MTTR on critical services) rather than headcount.
Final Tip — One-Control Sprint (4 Weeks)
Pick a single high-impact control, map it to DORA’s proportionality wording, right-size it and document your rationale. Repeat quarterly; proportionality will soon become muscle memory.